WhatsApp has been in the news recently for having a serious Remote Code Execution vulnerability exposed. If you haven’t yet then make sure that you update your apps, although unhelpfully the security fix wasn’t mentioned in the release notes.
I’ve previously written about how to change the default settings to improve privacy and there are some good write-ups on this topic following the security incident. Some other things that you may wish to disable are saving media to your gallery and the cloud backup of messages, which bypasses the End-to-End (E2E) encryption.
You can’t disable the daily local backup. This backup is saved to a location that is easily accessible by any app that has permission to read it (most of them). Fortunately, this backup file is encrypted and the key is in a location only available to the WhatApp app. It appears to be a custom encryption scheme, so we’ll see how secure it is (considering the security flaws already discovered).
Another way that the confidentiality of E2E encryption is compromised is when you send a link in a message and a preview is generated. This isn’t news and has been covered before based on network analysis but here is a method to demonstrate this easily to non-technical people.
In the UK (or if using a VPN to the UK) try sharing a link to BBC News in a WhatsApp chat. You may notice that although the URL is a .co.uk one the preview will be a .com one. That’s odd.

The astute reader has probably worked out what is going on here and deduced the consequences for confidentiality. This preview privacy leak happens before you even send a message. It occurs while you are typing, even if you decide not to send the link after all.
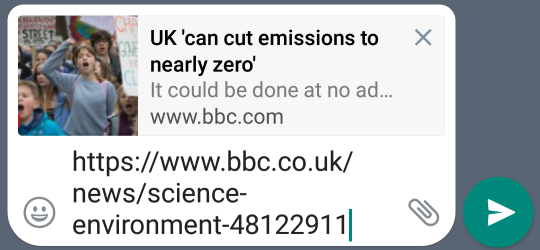
Due to the unique way that the BBC is funded you get a different view of it depending on which country you are in. From the UK you see the public service side but from overseas you see the BBC’s commercial arm. For the news site this means adverts and for iPlayer it means you can’t watch anything.
The preview for the link is being retrieved from outside the UK. Your URL is probably going via Ireland, where the corporation tax and data privacy regulations are very friendly to multinational enterprises.
WhatsApp is a native application and so doesn’t have to worry about the cross-origin (CORS) headers that browsers do. There is no technical reason for Facebook to proxy this request via their servers rather than have the app generate this preview directly itself.
However, there are many business reasons why Facebook may wish to see the plain text links in WhatsApp messages. What these may be is left as an exercise to the reader. It may be an interesting experiment to paste odd links into messages (but not always even send them) and see how this behaviour in WhatsApp affects adverts that are shown on Facebook or Instagram.
There are of course many good alternatives to WhatsApp. The best closest match is Signal but if you want something more collaborative than perhaps Slack is a better fit. A very promising alternative that fits into both camps is Riot/Matrix, which is approaching stable and should be significantly improved by the recent infrastructure rebuild following a security incident.